Between and I took 4756 steps.
IndieWeb post types
This content type is full of IndieWeb post types, which are all content types which allow me to take greater ownership of my own data. These are likely unrelated to my blog posts. You can find a better breakdown by actual post kind below:
Liked
Carol 🪩 (@carol@social.lol)
Post details
making my car microdose petrol cause i’m tapping my foot to the beat of the music
Reposted
Sheryl 2 Crows (John, he/him) (@LoganFive@beige.party)
Post details
Things that should burn more calories than they do: -Writing an email to someone you hate but have to work with -Being on the phone with insurance companies -Family gatherings -Cleaning your bathroom -Ennui -Trying to explain yourself Feel free to add more.
Liked
Pelle Wessman (@voxpelli@mastodon.social)
Post details
Anyone knows what, if anything, that’s holding back the Web Share Target API from Safari and Firefox? https://developer.mozilla.org/en-US/docs/Web/Manifest/share_target I would love to be able to install a bookmark manager as a PWA and easily share to it. Right now I would need to do quite some juggling with Apple Shortcuts to get a similar functionality Maybe one of @jensimmons@front-end.social, @tomayac@toot.cafe, @paul@status.kinlan.me knows?
Between and I took 7167 steps.
Liked
Ratchet & Clank Rift Apart: Best Settings for Steam Deck

Post details
60 FPS in Ratchet and Clank: Rift Apart on Steam Deck? Let's find out and dive into its performance and the best settings.

Between and I took 6704 steps.
Reposted
Forrest Brazeal (@forrestbrazeal@hachyderm.io)

Post details
Attached: 1 image idk why people say funding OSS is difficult

Reposted
Polynomial C (@Polynomial_C@mastodon.social)

Post details
Attached: 1 video This is why you have to avoid social networks with algorithms.

How has no one told me that Ratchet and Clank has a PC port after all these years?!?! BRB immediately downloading and playing it
Liked
The romance of Europe — brandur.org
Post details
A concert in Berlin, correcting for tourist bias, and how smartphones own the planet.
Listened to
Tars all the way down with Jon Johnson from Chainguard (Ship It! #105)

Post details
Jon “gzip enthusiast” Johnson joins us for a history lesson on compression & how it impacts everything from containers to Alpine.
Between and I took 11174 steps.
Listened to
The Business of Open Source | Using Open Source for Trust, not Growth, with Reshma Khilnani

Post details
This week on The Business of Open Source I spoke with Reshma Khilnani, CEO and founder of Medplum. Medplum is an open source electronic health record development platform, and one of the things I loved about this conversation is that Reshma is so focused on the healthcare industry — a level of...

Liked
Closed Captions (@closedcaptionsbot@mastodon.social)
Post details
[moaning]
Between and I took 6385 steps.
Liked
My BDFL guiding principles | daniel.haxx.se

Post details

Reposted
Kevin Beaumont (@GossiTheDog@cyberplace.social)
Post details
If you want to know where tech companies are with AI safety, know Microsoft Recall won’t record screenshots of DRM’d movies.. ..but will record screenshots of your financial records and WhatsApp messages, as corporate interests were prioritised over user safety. And it’s enabled by default.
Reposted
Lars Marowsky-Brée 😷 (@larsmb@mastodon.online)
Post details
We are more prone to anthromorphizing LLMs than to humanizing suffering humans
Liked
Chris "Not So" Short 🇺🇦 (@ChrisShort@hachyderm.io)
Post details
I just finished proofreading my personal Kubernetes 10th birthday blog post. It's 3000 words, and the Generative AIs like it well enough. It'll be up on chrisshort.net on June 6th. #Kubernetes
Liked
Rob Whitaker (@RobW@iosdev.space)

Post details
Attached: 3 images Went to a Lego show today. I had a great time!

Reposted
Mark Gibbings-Jones (@markx@toot.community)

Post details
Attached: 1 image

Reposted
Another Angry Woman (@stavvers@masto.ai)
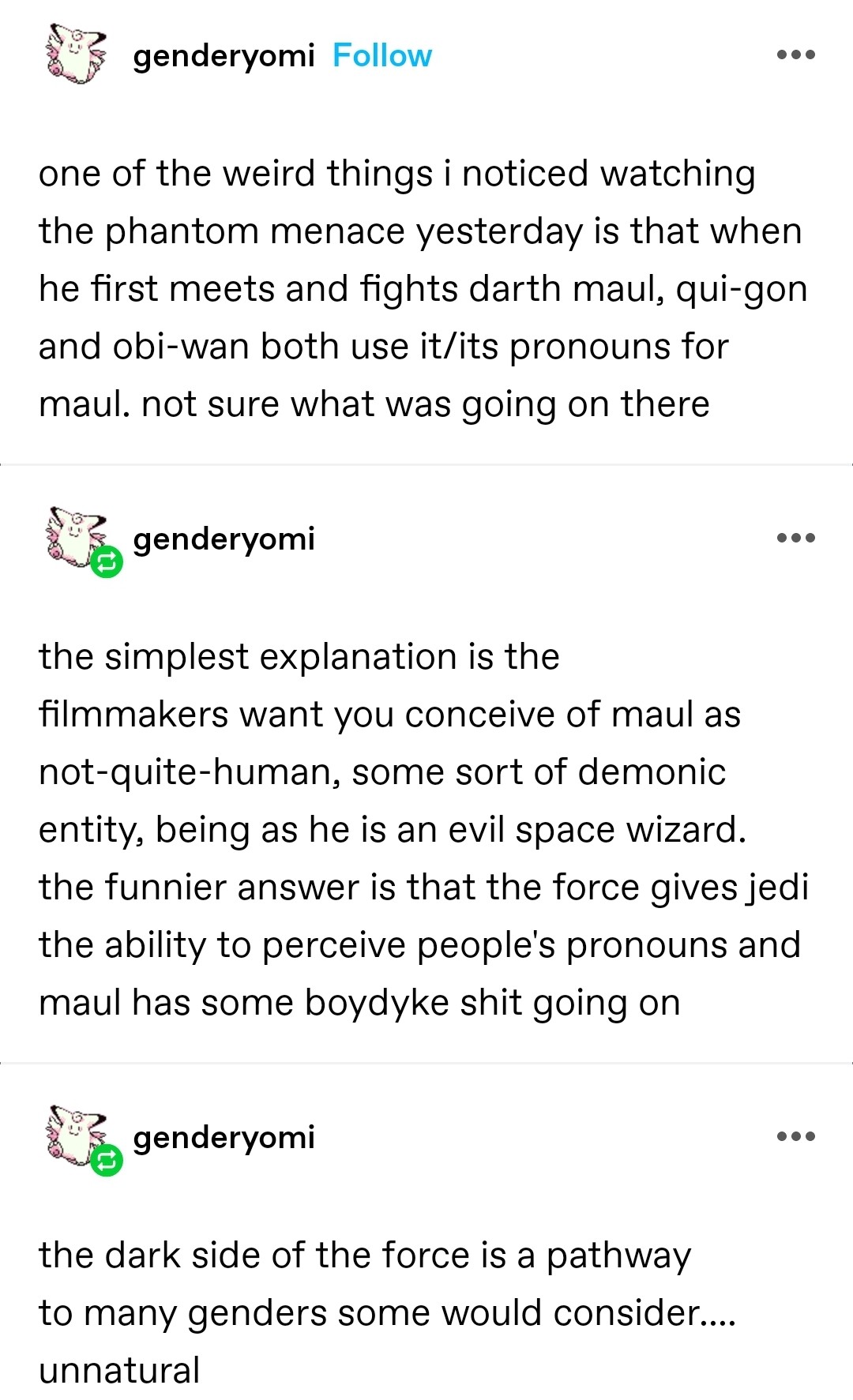
Post details
Attached: 1 image darth maul

Liked
ThatSexToyGuy (@hungry_joe@mas.to)
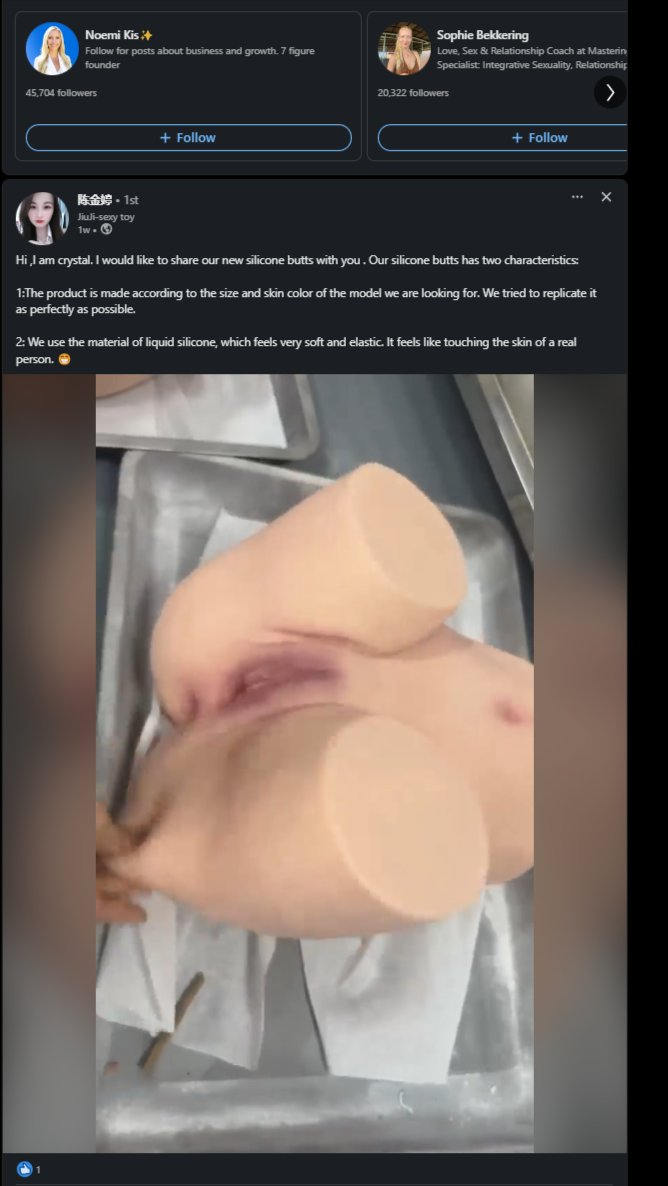
Post details
Attached: 1 image i literally can't open ANY social media in public. THIS IS MY LINKEDIN

Reposted
Adderall girl grindset (Jes) (@Jessica)

Post details
hot take linux is not harder than windows, most people are just blind to the sheer amount of upkeep that windows requires.
Listened to
It's a long & windy road with Shaundai Person at Microsoft Build 2024 (Changelog & Friends #45)

Post details
We kick off our Microsoft Build 2024 “coverage” in this free-wheelin’ conversation with our friend, Shaundai Person! We’re talking Netflix infra, we’re talking sales, we’re talking real-world AI usage, we’re talking career choices…. What’s a good next step? Listen in!
Liked
GitHub - qualified/lsps: Use Language Servers with in-browser editors. Monorepo of editor agnostic packages and CodeMirror client.

Post details
Use Language Servers with in-browser editors. Monorepo of editor agnostic packages and CodeMirror client. - qualified/lsps
Listened to
The Secret Sauce | The Secret Behind Kubernetes with Kelsey Hightower

Post details
In today's episode, Kelsey Hightower discusses the evolution of Kubernetes, the importance of open source, and the future of technology, including AI. Join the conversation as Kelsey shares insights on the tech industry, open source sustainability, and the impact of AI on our daily lives. Check...

Between and I took 7547 steps.
Reposted
Patrick Johanneson 🚀 (@pjohanneson@mstdn.ca)
Post details
@jalcine@todon.eu @wxcafe@social.wxcafe.net If it's ethical for the companies to use AI, it's ethical for you to subvert it.
Reposted
Danielle Foré (@danirabbit@mastodon.online)
Post details
The more I think about it, the major problems in tech and in society in general is that all the investment is going to solve problems that white affluent men have
Liked
bert hubert 🇺🇦🇪🇺 (@bert_hubert@fosstodon.org)
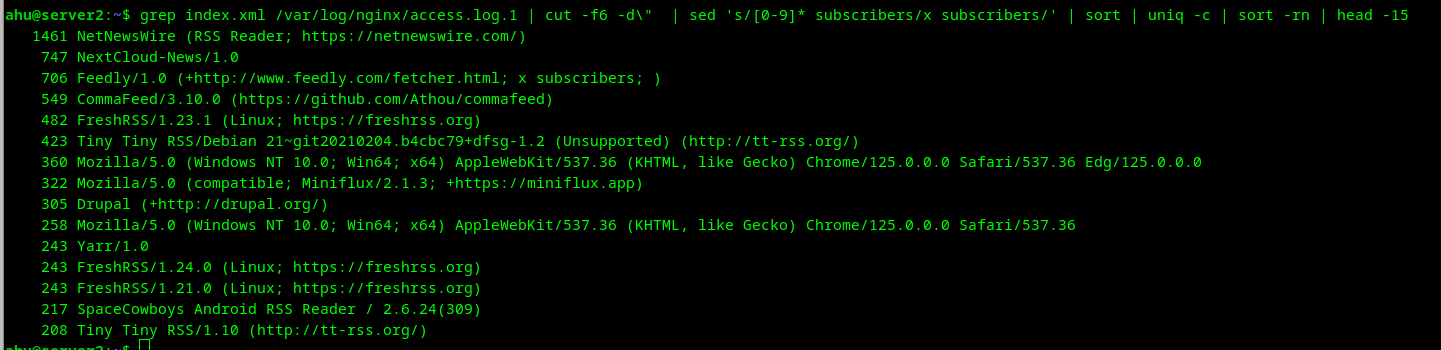
Post details
Attached: 1 image Two days ago I created a blog post which I did not promote in any way, but it did appear on my RSS feed. It now has over 6000 visitors. There are 15000 requests for the RSS feed every day, coming from the user agents listed below. RSS might not be dead yet.

Liked
Chris Fletch :pentagram: (@HailsandAles@metalhead.club)
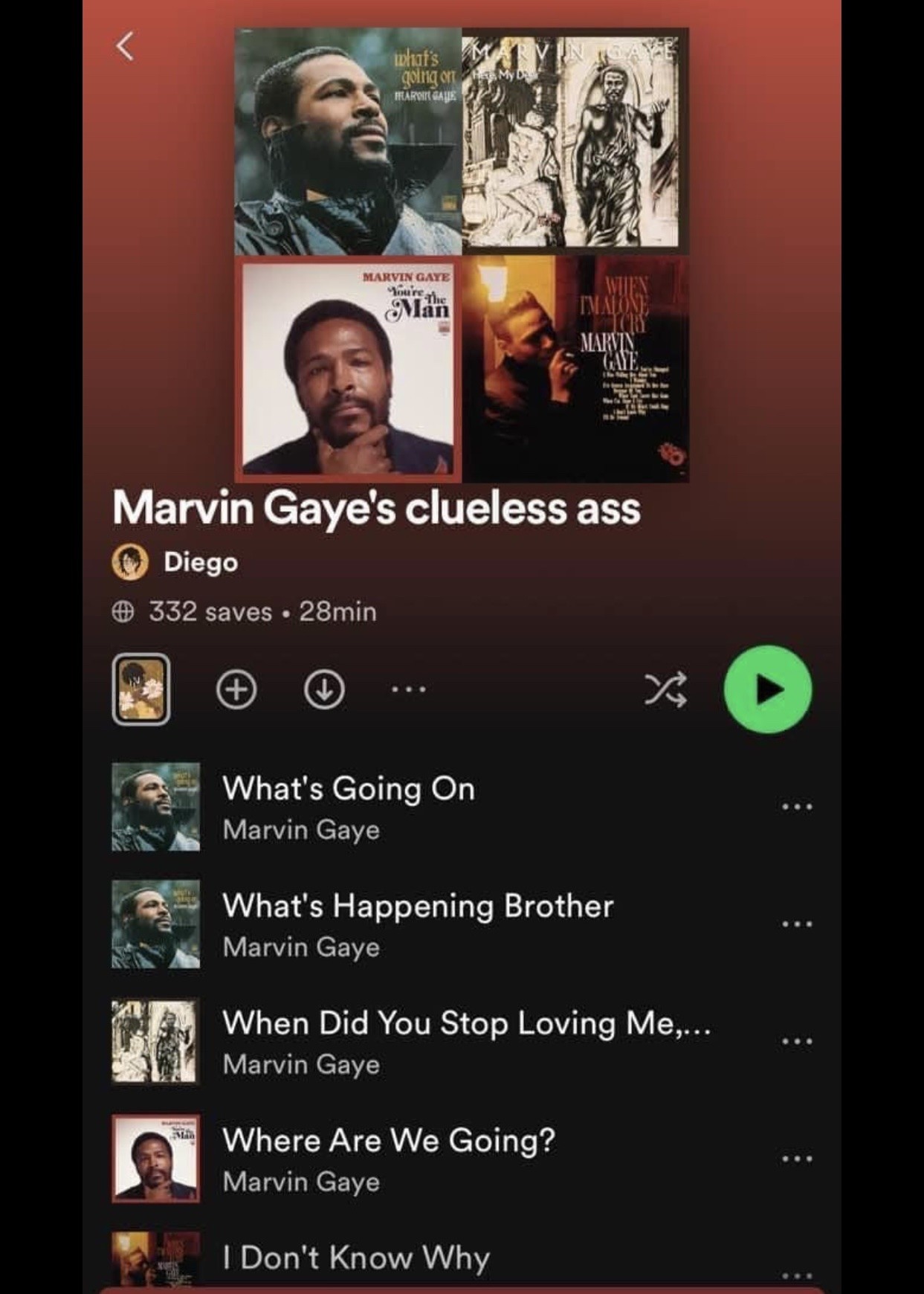
Post details
Attached: 1 image Best playlist I’ve saw

Reposted
Kyle Rankin (@kyle@kylerank.in)
Post details
Burnout in the FOSS community is real, and I'm glad that it's something that is being talked about more in blogs and conferences. There is a different flavor of burnout and emotional toll when you are sacrificing for a cause you believe in (especially in FOSS where people are often working for free or at below market rate). Working for a cause you believe in brings the highest highs when things are going well, but the lowest lows when they go badly. #FOSS #burnout
Listened to
Cup o' Go | 🕸️ With great power comes great responsibility, or why not to use the linkname directive 🔗

Post details
ProposalsAccepted: require Linux 3.17 kernel for Go 1.24Previous discussion: Episode 61Accepted: add encoding.AppendText and encoding.AppendBinaryPrevious discussion: Episode 62Accepted: add HostLayout directive type🪟 Accepted: Normalize line endings in example output comparisonsConference...

Listened to
Migrating from PHP to Go with Matthew Boyle & Chris Shepherd (Go Time #316)

Post details
Based on their experience in Curve and Cloudflare, Matthew Boyle & Chris Shepherd share their experience migrating from PHP to Go.
Liked
Chris's Wiki :: blog/programming/Go123LinknameComingProblem
Post details
Liked
Patricia Aas (@Patricia@vivaldi.net)
Post details
I think this book affected me in a completely opposite direction of what was intended. I am extremely motivated to make monolithic apps now. Brb gonna write a blog post on my distributed app hosted in a single process doing synchronous message passing through compiler generated stubs (*cough* function calls) and how running my “distributed app” in the same virtual memory space lends itself to improved performance, monitoring and debugging. Imma call it Virtual Distributed Monolith. Pay me to be your consultant 💰 I’ll just write bs blog post like: “Real Time Audio with personalized addressing system allowing instant multichannel audio collaboration”
Liked
Terence Eden (@Edent@mastodon.social)

Post details
Attached: 1 image Holy shit! I found an Easter Egg in the latest #DoctorWho! (No spoilers for 73 Yards) There's a QR code on the table. But it has been damaged so it can't be scanned. If you repair it, it goes to the website of one of the production designers 😆

Listened to
Weighing open source project funding options, from taxes to anarchy | IT Ops Query
by

Post details
Justin Warren is founder and principal analyst at PivotNine, a technology consulting and analyst firm based in Melbourne, Australia. Until 2023, he was a board member at Electronic Frontiers Australia, a non-profit national organization representing Internet users. At KubeCon North America last year, he asked a press conference panel of enterprise IT leaders what they were doing to compensate open source maintainers "so they don't starve to death."A self-described "filthy socialist," Warren favors a tax or tax-like system for funding open source libraries that are widely used but not full-fledged products -- especially when the alternative is an offer from a malicious actor maintainers can't refuse. Together, Warren and Beth explore various approaches to shoring up the maintenance, security and sustainability of open source software and discuss the future outlook for the industry in this episode.
Listened to
a post on geeking-out.simplecast.com
