Tag security
Post details
Yesterday I announced HACKED - Fixing hacked WordPress site Workshop. For details eventbrite.co.uk/e/hacked-fixin… TLDR; Join me on the 22nd & 29th of April for 2 sessions on identifying & fixing hacked WordPress sites. Early bird tickets on sale now.Tim Nash (@tnash)Wed, 17 Mar 2021 09:33 GMT
Post details
Followed a tutorial and put JWTs in localStorage? If the guy behind UNPKG wanted to, he could inject code to JS requests and collect all of your users JWTs. Same w/ any 3rd party scripts you use. 2B req/mo is a lot of tokens. I put that crap in signed, https, SameSite cookies.Ryan Florence (@ryanflorence)Fri, 12 Mar 2021 18:02 GMT
Post details
Forgotten password reminder, your password is:
Post details
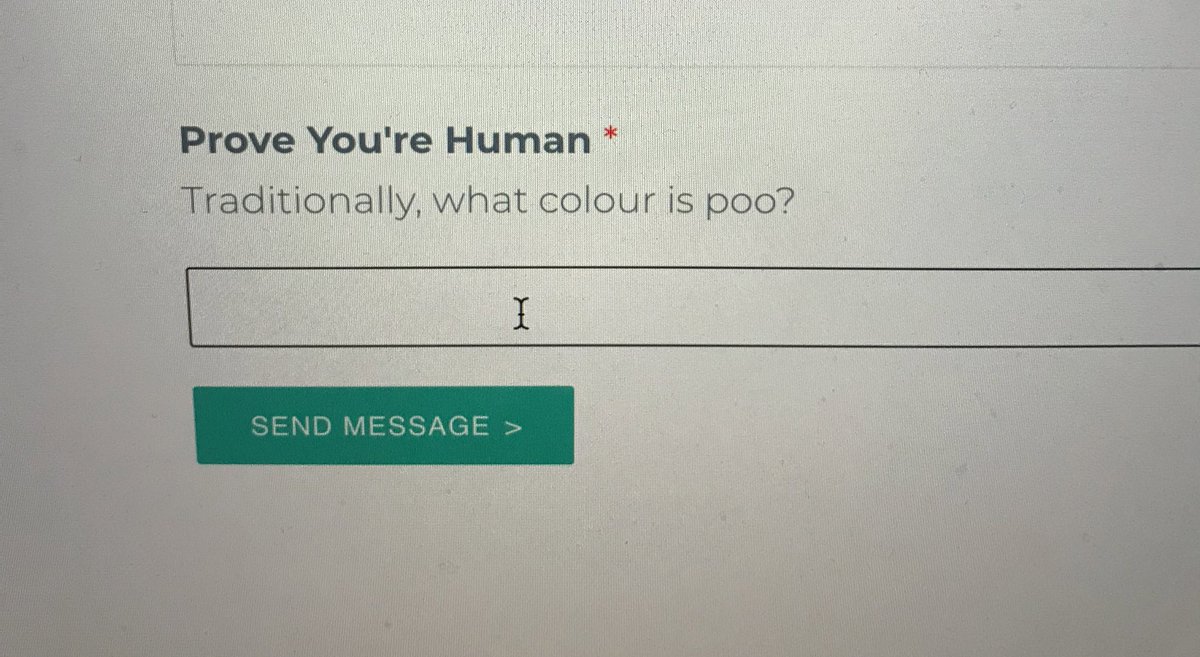
Tell us a cybersecurity horror story in 6 words.
Sophos (@Sophos)Wed, 03 Mar 2021 12:00 GMT
Matt Brunt (@Brunty)Sun, 07 Mar 2021 12:22 GMT
Post details
If it is this difficult to convince people to put a piece of fabric over their faces to prevent the transmission of disease so they don’t die or kill others… the outlook on getting humans to do all of those abstract, fiddly cybersecurity things required to be safe online is ☠️
Jessy Irwin ✨ (@jessysaurusrex)Fri, 05 Mar 2021 21:09 GMT
Encrypting and Decrypting Text with OpenSSL (2 mins read).
How to use openssl to encrypt text with a shared passphrase.
Post details
If an intern has the access and authority to make a mistake so critical that it pwns your org and all of your users, the fault is with leadership and everyone else upstream from that intern. The intern deserves an apology for being put in that position at all, not public shame.
Post details
Current and former top executives at SolarWinds are blaming a company intern for a critical lapse in password security that apparently went undiagnosed for years. The password in question, "solarwinds123," was discovered in 2019 on the public internet. cnn.it/3pWdZqxCNN (@CNN)Fri, 26 Feb 2021 23:35 GMT
Kat Cosgrove (@Dixie3Flatline)Sat, 27 Feb 2021 05:07 GMT
Post details
TIL that you no longer have to write <a target=“_blank” rel=“noopener”> to make external links secure! The HTML standard was changed in 2019 so that rel=“noopener” is always implied: github.com/whatwg/html/pu… thanks to the @jaffathecake and @DasSurma’s podcast for this tidbit!shawn swyx wang (@swyx)Thu, 28 Jan 2021 10:51 GMT
Post details
Well this is a new one
Rachel McConnell (@Minette_78)Tue, 26 Jan 2021 15:00 GMT
Post details
when you've forgotten your password
Stevie Martin (@5tevieM)Fri, 22 Jan 2021 20:32 GMT
Post details
WHAT. A Dutch researcher managed to log into @realDonaldTrump's Twitter account by guessing his password ("maga2020"), which had no 2-step verification. volkskrant.nl/nieuws-achterg…Charles Lister (@Charles_Lister)Thu, 22 Oct 2020 14:27 +0000
Post details
Well, _now_ it's a weak password.
Nathan "a specific and L.imited Way" Walls (@base10)Mon, 21 Sep 2020 19:39 +0000
Post details
This is really insightful. I've frequently run into exactly the same problem. Once the online tool is the only way somone knows to validate a secure token they will be more inclined to use it for sensitive data in a pinch
Post details
New blog post: Why I Actively Discourage Online Tooling like jwt.io and Online JSON Validators jvt.me/posts/2020/09/… (jvt.me/mf2/2020/09/ae…)Jamie Tanna | www.jvt.me (@JamieTanna)Tue, 01 Sep 2020 14:49 +0000
Andy March (@AndyMarch)Wed, 02 Sep 2020 12:57 +0000
Why I Actively Discourage Online Tooling like jwt.io and Online JSON Validators (5 mins read).

Why you should be opting for local tooling when working with sensitive data, even Non-Production ones.
Not sure how I feel with such a single point of failure, but an interesting idea nonetheless!
Post details
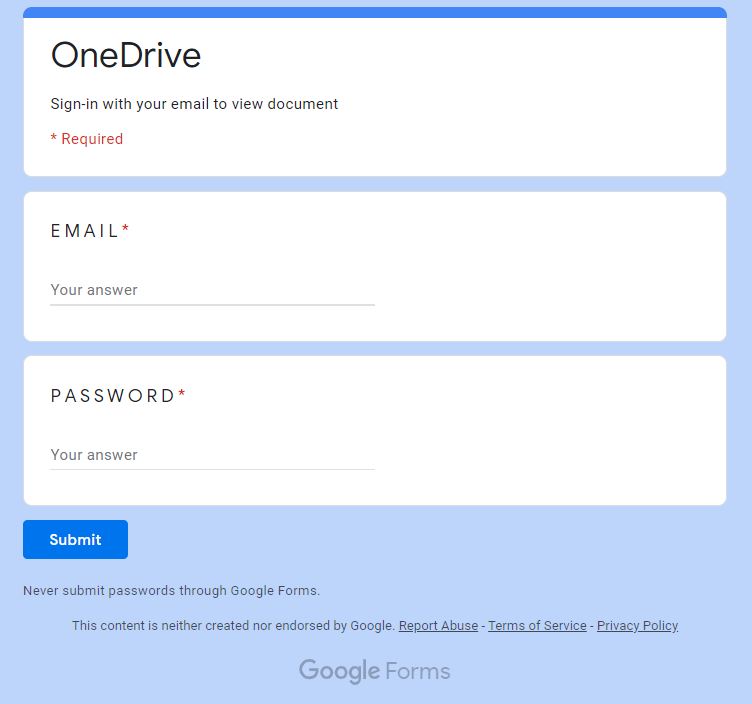
Found this on Reddit
Jackie! ✨ #FullStackInfosec (@find_evil)Wed, 22 Jul 2020 21:45 +0000
Post details
This has got to be one of the laziest phish I've ever seen.
alissa (@dnsprincess)Thu, 16 Jul 2020 22:05 +0000
Post details
I think it's super sweet that people are surprised the recent Twitter security incident was used to inflict relatively little damage. What if I told you that's how most AppSec exploits are used? I once watched a user get admin rights on a system and use it to reset her own pw
Rebecca Deck (@ranger_cha)Thu, 16 Jul 2020 13:04 +0000
Post details
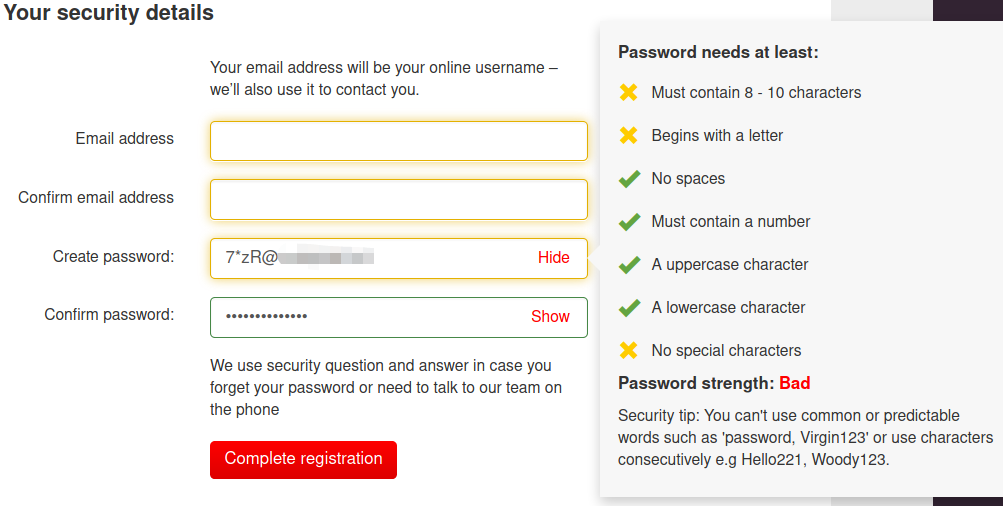
Virgin Mobile have an "interesting" approach to online account security. 📋 Can't paste in a password. 🔢 10 characters only. 🔣 No special characters. 🔤 *Must* start with a letter! I understand (but don't agree with) all the restrictions except the last one. What's that about?Terence Eden (@edent)Mon, 13 Jul 2020 10:04 +0000
Post details
private byte[] generatePrivateKey() { byte[] bArr = new byte[32]; Sodium.randombytes(bArr, bArr.length); Util.logByteArray(bArr); return bArr; } ARE YOU FUCKING SHITTING MEMatthew Garrett (@mjg59)Tue, 07 Jul 2020 08:56 +0000
Post details
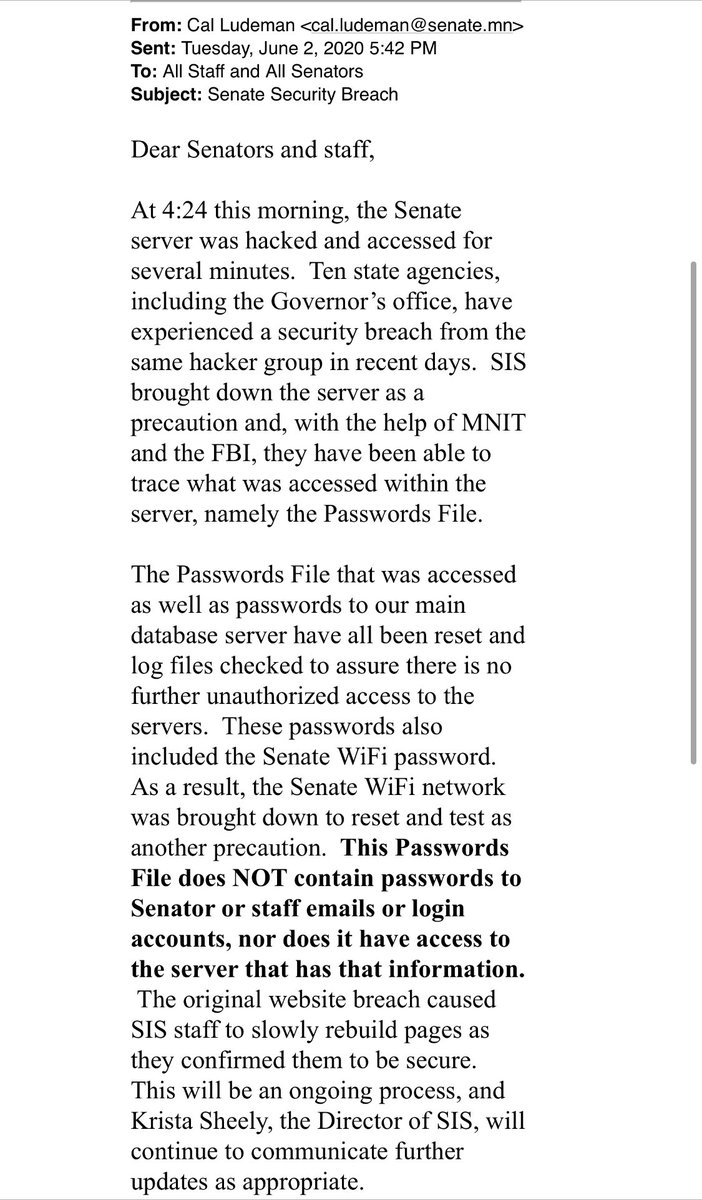
Hackers, can we all just take a moment to imagine the back end that must have existed to let something like this happen twitter.com/stowydad/statu…Post details
Minnesota Senate and some state agency web sites hacked. #mnlegBrian Bakst (@Stowydad)Tue, 02 Jun 2020 23:10 +0000
Ian Coldwater 📦💥 (@IanColdwater)Tue, 02 Jun 2020 23:21 +0000